Auth
Use Supabase to authenticate and authorize your users.
There are two parts to every Auth system:
- Authentication: should this person be allowed in? If yes, who are they?
- Authorization: once they are in, what are they allowed to do?
Supabase Auth is designed to work either as a standalone product, or deeply integrated with the other Supabase products. Postgres is at the heart of everything we do, and the Auth system follows this principle. We leverage Postgres' built-in Auth functionality wherever possible.
Here's a quick, 2 minute tour of the Auth features built-in to Supabase:
Authentication
You can authenticate your users in several ways:
- Password-based methods such as email or phone and password
- Passwordless methods such as sending a magiclink or one-time password (OTP)
- OAuth social providers
- SAML SSO
- Anonymous Sign-ins
Providers
We provide a suite of Providers and login methods, as well as Auth helpers.
Social Auth
Phone Auth
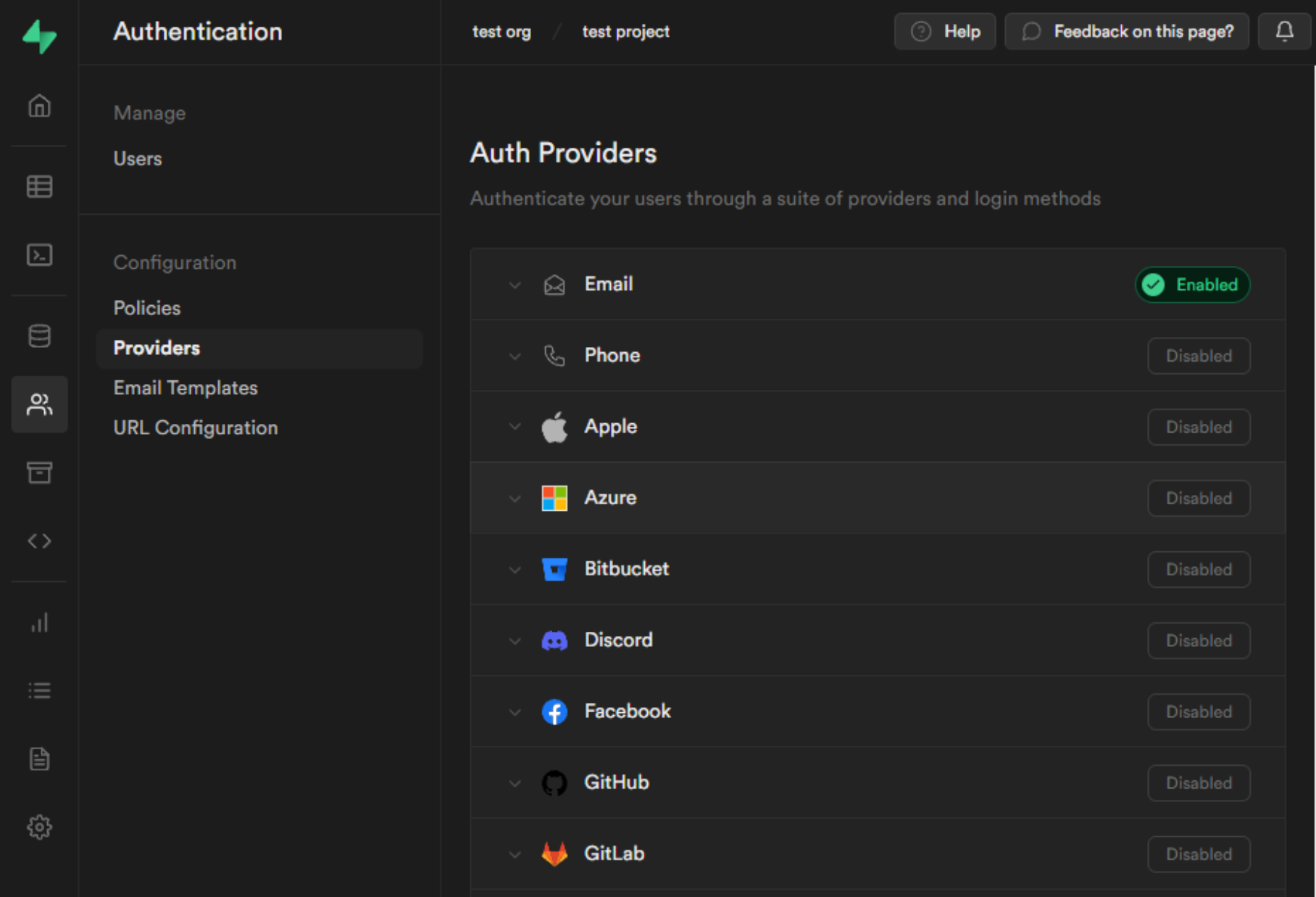
Configure third-party providers
You can enable third-party providers with the click of a button by navigating to Authentication > Providers > Auth Providers and inputting your Client ID and Secret for each.
Redirect URLs and wildcards
We've moved the guide for setting up redirect URLs here.
Netlify preview URLs
Vercel preview URLs
Mobile deep linking URIs
Authorization
When you need granular authorization rules, nothing beats PostgreSQL's Row Level Security (RLS).
Policies are PostgreSQL's rule engine. They are incredibly powerful and flexible, allowing you to write complex SQL rules which fit your unique business needs.
Get started with our Row Level Security Guides.
Row Level Security
Authentication only gets you so far. When you need granular authorization rules, nothing beats PostgreSQL's Row Level Security (RLS). Supabase makes it simple to turn RLS on and off.
Policies
Policies are PostgreSQL's rule engine. They are incredibly powerful and flexible, allowing you to write complex SQL rules which fit your unique business needs.
With policies, your database becomes the rules engine. Instead of repetitively filtering your queries, like this ...
_10const loggedInUserId = 'd0714948'_10const { data, error } = await supabase_10 .from('users')_10 .select('user_id, name')_10 .eq('user_id', loggedInUserId)_10_10// console.log(data)_10// => { id: 'd0714948', name: 'Jane' }
... you can simply define a rule on your database table, (select auth.uid()) = user_id, and your request will return the rows which pass the rule, even when you remove the filter from your middleware:
_10const { data, error } = await supabase.from('users').select('user_id, name')_10_10// console.log(data)_10// Still => { id: 'd0714948', name: 'Jane' }
How it works
- A user signs up. Supabase creates a new user in the
auth.userstable. - Supabase returns a new JWT, which contains the user's
UUID. - Every request to your database also sends the JWT.
- Postgres inspects the JWT to determine the user making the request.
- The user's UID can be used in policies to restrict access to rows.
Supabase provides a special function in Postgres, auth.uid(), which extracts the user's UID from the JWT. This is especially useful when creating policies.
User management
Supabase provides multiple endpoints to authenticate and manage your users:
- Sign up
- Sign in with password
- Sign in with passwordless / one-time password (OTP)
- Sign in with OAuth
- Sign out
When users sign up, Supabase assigns them a unique ID. You can reference this ID anywhere in your database. For example, you might create a profiles table referencing id in the auth.users table using a user_id field.